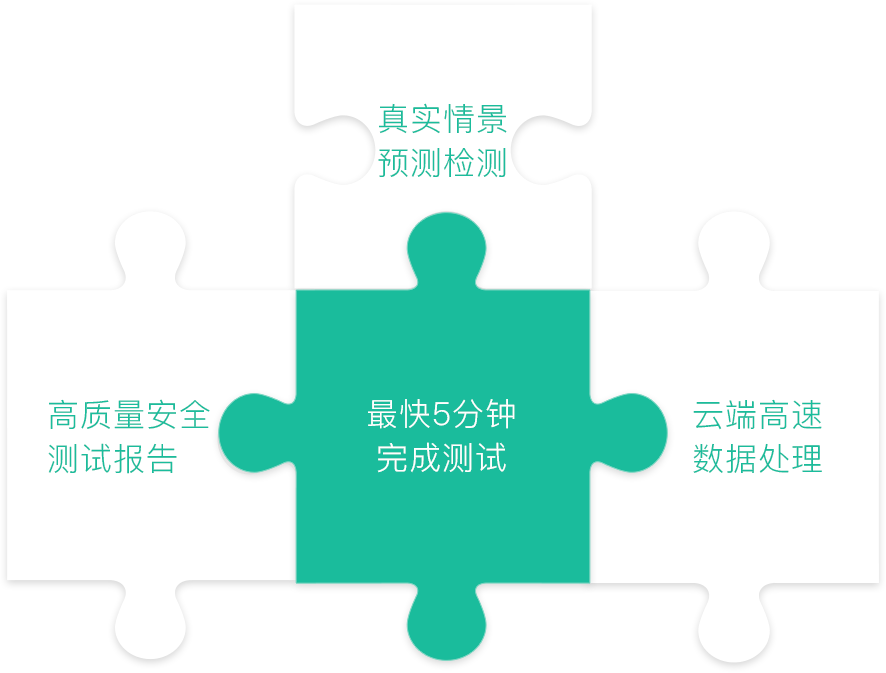
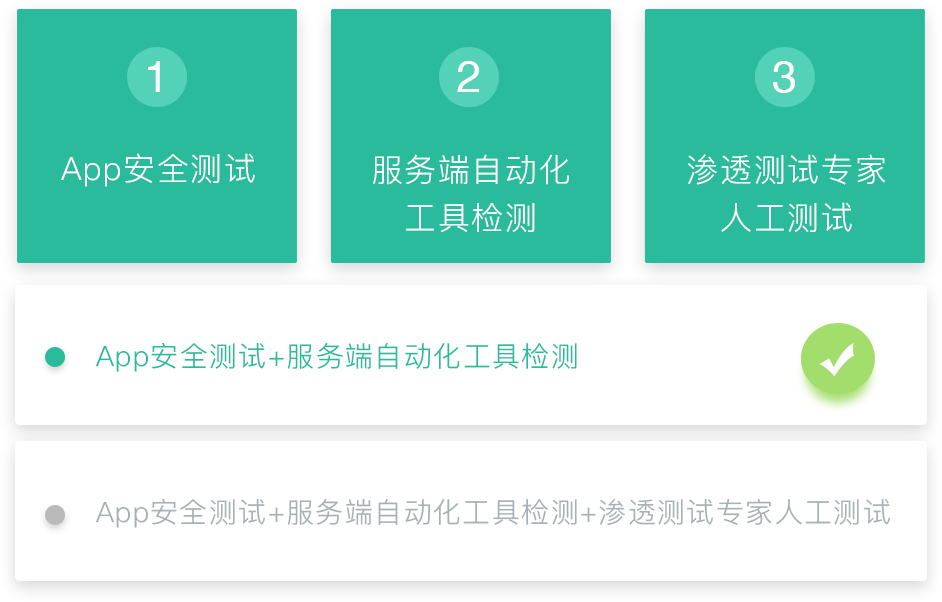
我们为移动应用App客户端执行自动化黑盒安全合规性测试,快速、精准地发现安全漏洞、风险和个人信息安全合规问题,由安全专家对服务端进行进一步深入的渗透测试,端到端的评估安全风险,并提供修复建议,帮助您在App发布前找到可能存在的安全缺陷、隐患与合规风险。

安全性事故频发

恶意抄袭、窃取信息
恶意注入程序造成用户损失

高额经济损失案件频发
专业高效去除安全隐患
 漏洞监测
漏洞监测 以静态漏洞扫描和动态执行的方式,检测App常见漏洞。
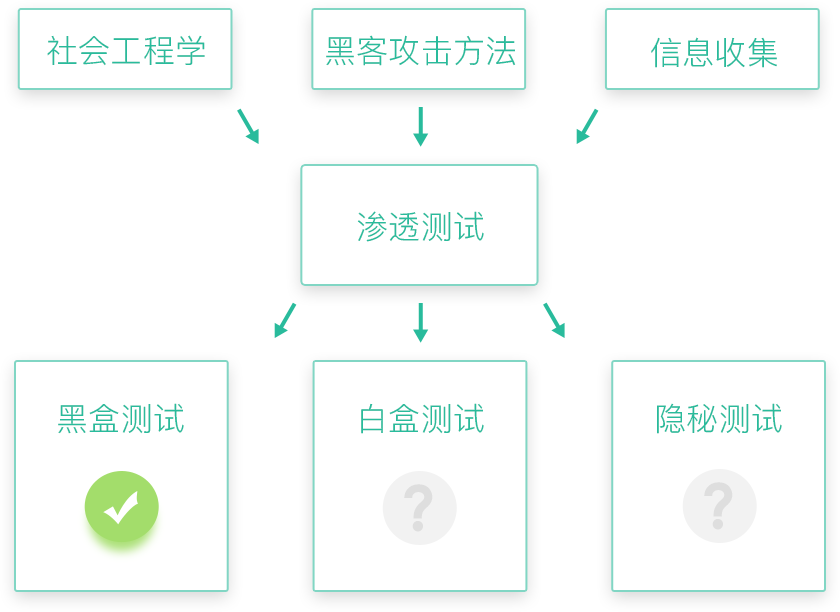
 渗透评估
渗透评估 对客户端、服务器、通信进行渗透测试,全面检测安全风险。
 修复建议
修复建议 对发现的安全漏洞及风险,提供可行的修复方案。
 专业报告
专业报告 测试完成后,生成包含漏洞信息的专业测试报告。
蒲公英专家测试 Copyright © 2026 蒲公英 陕ICP备15010407号